Norton Antivirus Internet Security 2007
2015 or 22.5.2.15 (Windows Edition), 4.0 (Macintosh Edition),WebsiteNorton Internet Security is a security program made by that protects from. It includes antivirus, firewall, e-mail filter, and phishing protection software. It also includes features like which can be downloaded as a add-on.Norton Internet Security was replaced by Norton Security in 2014.Norton Internet Security was available from a download, a in a store, or from a company that is an. Norton Internet Security and its sister product, combined, held a 61% market share as of 2007.
Major competitors in terms of market share include antivirus products from vendors, and.Norton Internet Security runs on. Version 22.5.2.15 was the last update available for Norton Internet Security for Windows computers. The latest Mac version is 4.0. Contents.Windows edition In August of 1990 Symantec acquired from. Norton and his company developed various utilities, or applications for.
Symantec continued the development of acquired technologies. The technologies are marketed under the name of 'Norton', with the 'from Symantec'. Norton's crossed-arm pose, a registered U.S. Trademark, was featured on Norton product packaging. However, his pose was later moved to the spine of the packaging, and later dropped altogether.was introduced to Norton Internet Security 2004, addressing the estimated 3.6 million counterfeit Norton products sold. A code is generated to identify a computer's configuration, which ties in with the product key. Users are allowed to activate their product five times with the same.
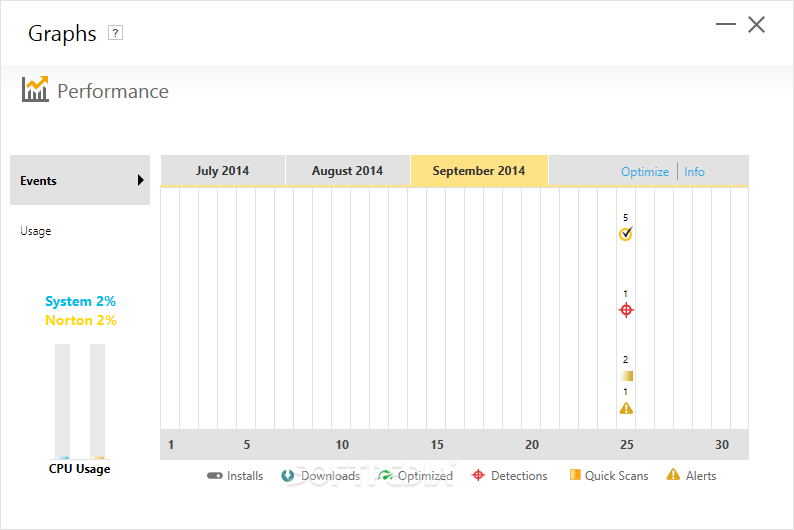
Detection and removal was introduced to the 2005 version for Windows, with the tagline 'Antispyware Edition'. The tagline was dropped in later.Existing users of the 2006, 2007, or 2008 versions can upgrade to the latest 2009 version without buying a new subscription. Upgrading will preserve the number of days left on a user's subscription. Version 2006 (13.0) Norton Internet Security 2006 debuted on September 26, 2005. The main, dubbed the Norton Protection Center aggregates all information in a central location. Reports the Norton Protection Center, while useful, attempts to advertise additional products and services from Symantec.To help identify, Bloodhound technology disassembles and scans application code for possibly malicious instructions. Norton can revert Internet Explorer attempts and block.
Users are warned of unauthorized changes to Internet Explorer's homepage, and given an option to revert such changes. Advertisement blocking rewrites a website's to prevent advertisements from being displayed. Scans mail for. It can be configured using either a or a. Users can also correct Norton's classification of e-mail on a individual basis. Parental controls, bundled with this release, allow users to block specific sites, block certain programs from accessing the, and restrict access. Norton can block the transmission of confidential information.
Users can enter information which are not to be communicated via, or.CNET noted this version's noticeable toll on system performance, especially when opening files across a network or on a removable disk. Oli Warner also noted Norton's significant drag when opening or creating files, compared to similar offerings from different vendors.
PC Magazine noted the program's lengthy installation time and weak spam filtering feature; valid e-mail messages were marked as spam and actual spam e-mail were not.compatibility was dropped from this release. System requirements were Service Pack 3 or, 325 of free space, a 300 MHz, and 256 MB of.Version 2007 (14.0) The 2007 version was released on September 12, 2006. 80 percent of the code was rewritten, with the goal of reducing high system resource utilization. A tabbed interface allows users to access the Norton Protection Center and the program settings without separate open. Symantec also extended its VxMS technology, enhancing detection. VxMS allows Norton to detect inconsistencies among files within directories and files at the volume level. Detection was introduced in this release for Internet Explorer.
Norton checks sites visited in Internet Explorer against a blacklist and analyzes sites' code. Other features include a scanner which looks at system components commonly hosting vulnerabilities, such as Internet Explorer settings.
Norton Internet Security Suite
Supplementing the scanner, real-time exploit protection blocks attackers from leveraging common browser and application vulnerabilities. When possible, Norton will fix issues found; otherwise the user is warned of the vulnerability. A startup application manager allows users to prevent applications from launching at login.E-mail spam filtering, parental controls, advertisement blocking, and the information filtering features were not bundled with this release to reduce performance impact and disk space requirements. Instead, the features are available separately in 2007 add-on package.reports mixed results in performance testing; however gains were made over the 2006 version.
Warner also noted the 2007 version's reduced impact on system performance, compared to the 2006 version. Similar to the prior version, spam filtering module misidentified valid e-mail and missed actual spam, according to PC Magazine.Windows 2000 compatibility was dropped from this release. Compatibility with 32-bit editions of Windows Vista was introduced later in this release with a patch from Symantec.
When installed in Vista, 350 MB of free space, an 800 MHz processor, and 512 MB of RAM is needed. When installed in Windows XP, 350 MB of free space, a 300 MHz processor, and 256 MB of RAM is required.Version 2008 (15.0) The 2008 version was released on August 28, 2007. New features include and the Norton Identity Safe. SONAR was designed using technologies Symantec acquired from. The Identity Safe supersedes the information filtering function, storing information and can fill such forms.
The information filtering feature is still available in the 2008 add-on package, and can be used in conjunction with the Identity Safe.Phishing protection now integrates with as well as Internet Explorer. The startup application manager was dropped from this release. Advertisement blocking was dropped from this release's add-on package.When installed in 32-bit editions of, 350 MB of free space, a 300 MHz processor, and 256 MB of RAM is required. Support for 64-bit editions of Windows Vista was added in this release. 350 MB of free space, a 800 MHz processor, and 512 MB of RAM is required.Version 2009 (16.0). This page or section needs to be.
Please help if you can. For tips on making this article better, read ' and '. ( April 2009)The 2009 version was released on September 8, 2008.
Conducted by PassMark Software highlights this release's 52 second install time, 32 second scan time, and 7 MB memory utilization. Symantec funded the benchmark test and provided scripts used to benchmark each participating.A single main interface replaces the tabs found in prior releases. New features include which files based on reputation, cutting scanning time. Updates are now delivered 5 to 15 minutes, supplementing the reliability tested updates issued by Symantec every several hours.
However, such updates may incorrectly identify files as malicious, and users can elect not to receive those updates. Spam filtering was reintegrated in this release. The add-on package now includes information filtering and parental controls.
The exploit scanner found in the 2007 and 2008 versions was dropped from this release.System requirements call for a edition of, a 300 MHz processor, 256 MB of RAM and 200 MB of free space. When installed in a 32 or 64-bit edition of Windows Vista, an 800 MHz processor, 512 MB of RAM, and 200 MB of free space is required.Notable new features include the integration of, a web rating service. Safe Web blocks access to malicious sites. Additionally, search results from major search engine, such as, are color coded for safety (green for safe site, yellow for possibly unsafe site, red for dangerous sites, and gray with a white question mark for untested sites). The toolbar redirects queries to the, however does not share code with the Ask.com toolbar.
Kme diego software deutsch. Macintosh edition Version 1.0 through 3.0 Norton Internet Security version 1.0 for Mac was released November 1, 2000. It can identify and remove both Windows and Mac. Other features include a firewall, advertisement blocking in the, parental controls, and the ability to prevent confidential information from being transmitted outside the computer. Users are prompted before such information is able to be transmitted.
The incorporation of iClean allows users to purge the browser cache, and browsing history within Norton's interface. Operating system requirements call for Mac OS 8.1. Hardware requirements call for 24 MB of RAM, 12 MB of disk space, and a processor.Version 2.0 also ties in with the database, allowing users to trace attacking computers.
Free Norton Internet Security Antivirus
Users can inform network administrators of the attacking computers for corrective actions. When running under or, a PowerPC processor, 24 MB of RAM, and 25 MB of free space is required. Under, a processor, 128 MB of RAM, and 25 MB of free space is required.The subsequent release, version 3.0, maintained the feature set found in version 2.0. The firewall now allocates internet access as needed rather than relying on user input using predefined rules. Compatibility with OS 8 was dropped.
When running under OS 9.2, a PowerPC processor, 24 MB of RAM, and 25 MB of free space is required. Under OS X 10.1.5 through 10.3, a PowerPC G3, 128 MB of RAM, and 150 MB of free space is required. However, version 3.0 is not compatible with, or 'Tiger'. Version 4.0 Version 4.0 was released on December 18, 2008.
Symantec also markets a bundle of Version 4.0 and the 2009 version for Windows, intended for users with both Microsoft Windows and Mac OS X installed. IClean was dropped from this release. The firewall now blocks access to malicious sites using a blacklist updated by Symantec. To prevent attackers from leveraging insecurities in the Mac or installed software, exploit protection was introduced in this release.
Phishing protection was introduced in this release as well. Operating system requirements call for Mac OS X 10.4.11 or higher. Either a PowerPC or processor, 256 MB of RAM and 150 MB of free space are required.Reception FBI cooperation The confirmed the active development of, a intended to obtain passwords to encrypted e-mail as part of a criminal investigation. Magic Lantern was first reported in the media by of on 20 November 2001 and by Ted Bridis of the. The FBI intends to deploy Magic Lantern in the form of an.
When the attachment is opened, it installs a on the suspect's computer. The trojan horse is activated when the suspect uses encryption, often used to increase the security of sent e-mail messages.
When activated, the trojan horse will log the PGP password, which allows the FBI to decrypt user communications. Symantec and other major antivirus vendors have whitelisted Magic Lantern, rendering their antivirus products, including Norton Internet Security, incapable of detecting Magic Lantern. Concerns include uncertainties about Magic Lantern's full potential and whether hackers could subvert it for purposes outside the jurisdiction of the law.Graham Cluley, a technology consultant from, said 'We have no way of knowing if it was written by the FBI, and even if we did, we wouldn’t know whether it was being used by the FBI or if it had been commandeered by a third party'. Another reaction came from Marc Maiffret, and cofounder of, 'Our customers are paying us for a service, to protect them from all forms of malicious code.
It is not up to us to do law enforcement's job for them so we do not, and will not, make any exceptions for law enforcement malware or other tools.' FBI spokesman Paul Bresson, in response if Magic Lantern needed a court order to deploy, 'Like all technology projects or tools deployed by the FBI it would be used pursuant to the appropriate legal process.' Proponents of Magic Lantern argue the technology would allow law enforcement to efficiently and quickly decrypt messages protected by encryption schemes. Implementing Magic Lantern does not require physical access to a suspect's computer, unlike, a predecessor to Magic Lantern, since physical access to a computer would require a court order. Performance impact In 2006, Oli Warner published two articles comparing the system performance impact of various Windows applications, including.
He later reran the experiments, revising his methodology and included at Symantec's request.Warner benchmarked the processor and the disk performance with and without each application, compiling two scripts in, a. One calculated all between 100,000 and 200,000 and the other tested file read/write time. Was used to measure boot time. All testing was conducted inside a environment created. Despite the 2007 version's improvements, Warner noted its significant boot delay and impact on file operations.Recent testing conducted by PassMark Software found the 2009 version had the least impact on system performance. As noted earlier, Symantec funded the testing and provided some of the scripts used. Warner's scripts were also used to test file read/write time.
The second and third ranked suites were and, respectively. Systems were benchmarked with a clean installation of Windows Vista, then again with a security suite installed. The 2009 version had the least impact on boot time, the fastest scan speed, lowest memory utilization, and the program itself installed the fastest out of its competitors. However, the 2009 version had the second most impact on file read/write time, as highlighted by Warner earlier. Uninstallation Norton Internet Security (Windows versions) have been criticized for refusing to uninstall completely, leaving unnecessary files behind.
Versions prior to 2009 installed a separate program, which updates Norton-branded software. The user must uninstall both Norton Internet Security and the LiveUpdate component manually. The LiveUpdate component is purposely left behind to update other Norton-branded products, if present. In response, Symantec developed the to remove leftover keys and values along with files and folders.
Uninstallation will not remove subscription data, preserved to prevent users from installing multiple trial copies.Windows XP and Vista Service Packs When is installed, users encountered incompatibilities upgrading to. Users report numerous invalid keys being added by a tool named fixcss.exe, resulting in an empty Device Manager and missing devices such as wireless network adapters. Symantec initially blamed Microsoft for the incompatibilities but has since accepted partial responsibility.Dave Cole, Symantec's senior director of product management, acknowledged that users running Norton products were experiencing problems, but said the numbers are small. Cole also said that Symantec had done 'extensive testing' of its products with Windows XP SP3, but this issue had not surfaced. Cole essentially blamed Microsoft, 'This is related to XP SP3,' he stated. Microsoft recommended users to contact Windows customer support.
To resolve the problem, Symantec has issued a fix intended for users before upgrading. Symantec also recommends disabling the tamper protection component in the 2008 release, dubbed SymProtect. A tool to remove the added registry entries is also available from Symantec. Windows Vista Sarah Hicks, Symantec's vice president of consumer product management, voiced concern over Windows Vista 64-bit's feature. PatchGuard was designed by Microsoft to ensure the integrity of the, a part of a which interacts with the hardware. Often hide in a operating system's kernel, complicating removal.
Mike Dalton, European president of said, 'The decision to build a wall around the kernel with the assumption it can't be breached is ridiculous', claiming Microsoft was preventing security vendors from effectively protecting the kernel while promoting its own security product,. Hicks said Symantec did not mind the competition from OneCare. Symantec later published a white paper detailing PatchGuard with instructions to obtain a PatchGuard exploit.
After negotiations and investigations from antitrust regulators, Microsoft decided to allow security vendors access to the kernel by creating special instructions. References.