Hack Asp Using Sql Injection Tool
Filme morte subita download dublado 1995. Now basically what a dork does is uses Google’s “inurl” command to return websites which have a specific set of vulnerable words in url. For that, we need to know which words in the url make a website potentially vulnerable to a SQL injection attack. Many websites offer a comprehensive list of google dorks.
For example, thewebsite has a list of hundreds of google dorks. However, creativity is your best tool when it comes to finding vulnerable sites, and after practicing with some google dorks, you will be able to create your own. A few dorks have been listed below. What you have to do is paste them into the google search bar and google will return potentially vulnerable sites. NOTE: Don’t mind the root@kali:# behind the code.
I have implemented this on all the code on my blog, and the majority of it is really on Kali Linux so it makes sense there but not here. Inurl:”products.php?prodID=” inurl:buy.php?category= What you have to notice here is the structure of the commands.
The inurl instructs google to look at the URLs in it’s search index and provide us with the ones which have a specific line in them. Inside the inverted commas is the specific URL which we would expect to see in a vulnerable website. All the vulnerable sites will surely have a.php in their URL, since it is an indicator that this website uses SQL database here. After the question mark you will have a?something= clause. What lies after the = will be our code that is known to cause malfunctioning of databases and carrying out of a Sql Injection attack.
After you have used the dork, you have a list of potentially vulnerable sites. Most of them though, may not be vulnerable (i.e not the way you want them to be, they might still be having some vulnerabilities you don’t know about yet). The second step is finding the actually vulnerable sites from a list of possible ones. Testing sites for vulnerabilities. From here on, the things will get tough if you are not able to follow what I’m doing. So, we will unify under a single website. This website is intentionally vulnerable to SQL injection, and will prove highly useful since we will be doing the same thing.
The purpose of introducing this site at a later stage was to give you an idea how to find vulnerable sites yourself and also find the vulnerable columns. This is what will prove useful in real life. However, to make what follows comparatively easier, we all will now hack the same website. The website is.
This is what you vulnerable page looks like to start with As you can guess, it is vulnerable to SQL injection attack Now we need to find the number of columns. Nothing so far.
So if there was an error on 12th columns. This means there were 11 columns total. So to find the vulnerable column, we have to execute – This does not return any error. As I said before, adding a minus sign (-) after = and before 1 will help.
Now we can see total four numbers on the page. 11,7,2 and 9. It won’t be hard to figure out which of them depicts the vulnerable column You can take a look at the page (no minus sign that is). Now scroll down to the bottom. You will see this.
Comparing the pic with and without the error, we can easily say that the unexpected element in the malfunctioned page is the number 11. We can conclude that 11th column is the vulnerable one.
These kind of deductions make hacking very interesting and remind you it’s more about logic and creativity than it’s about learning up useless code. Now we are finally where we left out before we changed our stream.
We need to find the sql version. It can sometimes be very tricky. But lets hope its not in this case.
Now get the code that told you about the vulnerable column and replace the vulnerable column (i.e. 11) with @@version.
Sql Injection Tutorial Pdf
The url will look like this. Now finally you’ll see something like. The server is using Sql version 5.1.69, most probably MySQL (pretty common). Also we know the OS is Ubuntu. And the thing I said about it being tricky sometimes. Sometimes the server does not understand the @@version command directly and you need to convert it. You will need to replace @@version with convert(@@version using latin1) or unhex(hex(@@version)).
Now the information gathering part is complete. We have to move to actual download of tables.
Just write down all you know about their database, table and server. You must have a real sense of accomplishment if you have followed the tutorial so far. The boring part always requires maximum motivation and determination. Extracting tables from SQL database.
We now have the names of all the tables. Here it is – CHARACTERSETS,COLLATIONS,COLLATIONCHARACTERSETAPPLICABILITY,COLUMNS,COLUMNPRIVILEGES,ENGINES, EVENTS,FILES,GLOBALSTATUS,GLOBALVARIABLES,KEYCOLUMNUSAGE,PARTITIONS,PLUGINS,PROCESSLIST,PROFILING, REFERENTIALCONSTRAINTS,ROUTINES,SCHEMATA,SCHEMAPRIVILEGES,SESSIONSTATUS,SESSIONVARIABLES,STATISTICS, TABLES,TABLECONSTRAINTS,TABLEPRIVIL As you see, the ending of the last table is incomplete. To correct this, you can modify the end of the url to something like +from+informationschema.tables+where+tableschema=database Obtaining columns. It is similar to obtaining tables, other than the fact that we will use informaitonschema.columns instead of informaitonschema.tables, and get multiple columns instead of just one using the same group concat. We will also have to specify which table to use in hex. We will use the table events (I’ve highlighted it above too).
In hex it’s code is 45 (You can use text to hex convertor – also prefix 0x behind the code before entering it). The final code will be-. Columns+where+tablename=0x45 We now know the columns of the table events Extracting data from columns. We will follow the same pattern as we did so far.
We had replaced the vulnerable column (i.e. 11) with tablename first, and then columnname. Now we will replace it with the column we want to obtain data from. Lets assume we want the data from the first column in the above pic, ie. We will put the fol. URL- The page didn’t display properly, this means that the our query was fine.
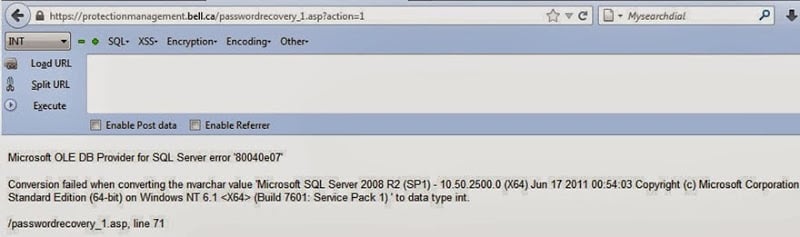
The lack of any data is due to the fact that the table was actually empty. We have to work with some other table now. Don’t let this failure demotivate you. However, our luck has finally betrayed us, and all this time we have been wasting our time on an empty table.
So we’ll have to look at some other table now, and then look at what columns does the table have. So, I looked at the first table in the list, CHARACTERSETS and the first column CHARACTERSETNAME. Now finally we have the final code as-. CHARACTERSETS This table has a lot of data, and we have all the charactersets name. So finally now you have data from CHARACTERSETNAME column from CHARACTERSETS table. In a similar manner you can go through other tables and columns.
It will be definitely more interesting to look through a table whose name sounds like ‘USERS’ and the columns have name ‘USERNAME’ and ‘PASSWORD’. I would show you how to organize results in a slightly better way and display multiple columns at once.

This query will return you the data from 4 columns, seperated by a colon (:) whose hex code is 0x3a., DEFAULTCOLLATENAME,0x3a,DESCRIPTION,0x3a,MAXLEN)+from+informationschema.CHARACTERSETS.
. Checking for Union Select Function.We will need our vulnerable column number here.Above we got 4 i.e 1,2,3,4-Now we need to find the injectable columns.To do that, site url followed by union select function and the vulnerable columns and also followed by our two hyphens (-). union select columns -Full URL: union select 1,2,3,4-After doing executing the url. We will need to study the page to find the numbers that appear because they are our only gateway to inject commands to the database.
Study the image: Normal and After Query. Now user CHAR(117, 115,101, 114, 115)DoneLet's continue our query.Replace parameter with and 1=2 union select 1,groupconcat(columnname),3,4 from informationschema.columns where tablename=CHAR(117, 115, 101, 114, 115)-Note: table name: users have been converted.Full URL: and 1=2 union select 1,groupconcat(columnname),3,4 from informationschema.columns where tablename=CHAR(117, 115, 101, 114, 115)-Result: ID,username,email,password,about,privilege,avatar,USER,CURRENTCONNECTIONS,TOTALCONNECTIONS. Hey, this is a really well written out guide and I'd like to thank you for it! However, I ran into one problem about halfway through.
I finished getting user, directory, and version, now I was replacing the parameters and I was taken back to the original error when you put an apostrophe. This is my url line, what did I do wrong?obits.php?id=-1 and 1=2 union select 1,2,3,4,5,6,7,8,9,10,11,12,group concat(tablename),14 from information schema.tables where tableschema=database-edit: this is the error that pops upWarning: Invalid argument supplied for foreach in /var/www/htdocs/examplewebsite.ca/obits.php on line 34 Reply.
Is there any way to hack the website written using this code? Apostrophe method isn't working. I am gettingthe following errors:-1). You must provide username/mobile number and password2). Password must be at least 6 characters long3). This username doesn't exist in our database4).
The password does not match our recordUsername:Password:Please help me, I'm a newbie.Thank You So Much in Advance.